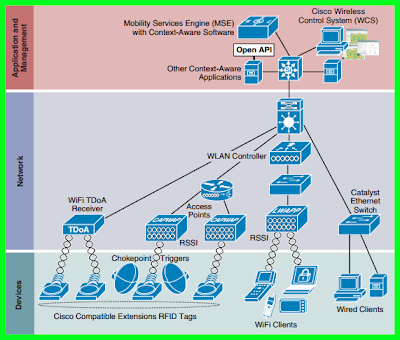
Cisco's acquisition of Meraki is an interesting prospect for customers, partners and competitors. Meraki are an unknown quantity to many, so I thought I would share my opinion on what this means to the WLAN industry.
As a WLAN engineer that has been working with Cisco for 10 years I'm pretty happy about it. I have been looking at Meraki for a while and picked up one of their AP's a few weeks ago. If you read my blog about BYOD you'll see I have a lot of love for the Meraki product.
Meraki have taken the controller to the cloud, they look after it. You choose upgrade windows and never have to pay for resiliency, new hardware, software upgrades or power bills. You can also buy switches and security gateways for the full feature set. All are cloud managed through a clean and simple web GUI. The main selling points of the solution are as follows:
- Plug and play access points (DHCP to Internet is all you need)
- Switch and security gateway appliances for additional features
- Feature-rich WLAN services - URL filtering, firewall, VPN
- Slick cloud-based management GUI
- BYOD out of the box - including the illusive trusted CA (see Building BYOD blog part 2)
- Free MDM for iPhone, Android, Windows, OS X
- Layer 2-7 stats and reporting
Cisco's ageing WLC-centric infrastructure has been struggling to compete in the SMB channel for a while now. For the last few years companies like Aruba, Aerohive and Ruckus have been turning heads. However, they will now lose many of their (compelling) arguments against Cisco's previously appliance-heavy infrastructure.
The $1.2bn price tag will be questioned, but I feel that this acquisition is vital to Cisco's strong position in the WLAN industry - and worth the investment. By acquiring Meraki, Cisco will be able to wade back into the SMB market. I can only see them expanding their customer base.
Cisco partners will be saying "Awesome, now we can offer BYOD and MDM at low cost".
Cisco competitors will be saying "Damn... We had them on the ropes...".
Meraki partners may be saying "Meh… Now we're going to lose out to Cisco Gold partners"
What does it mean for Meraki products and customers?
Anyone who has recently bought into the Meraki revolution might be worrying about what this acquisition means to them. If it is anything like the Airespace acquisition it will go like this:
- Cisco will rebadge the Meraki products and maintain current pricing.
- Cisco will honour all current support contracts. Support will be migrated to Cisco TAC.
- Cisco will phase out the Meraki hardware for Cisco hardware, then offer migration deals.
We're all trying to envisage what Cisco will attempt to do with Meraki. They may leave them to operate in isolation. As is stated by Meraki here http://www.meraki.com/company/cisco-acquisition-faq
I don't think cloud networking will extend into the Cisco product set quickly. However, there is nothing to stop network appliances being offered with 'local' or 'cloud' firmware. Much the same as autonomous or lightweight AP's today. However, Cisco will need carefully manage how they offer these products to customers.
I don't think cloud networking will extend into the Cisco product set quickly. However, there is nothing to stop network appliances being offered with 'local' or 'cloud' firmware. Much the same as autonomous or lightweight AP's today. However, Cisco will need carefully manage how they offer these products to customers.
The shift from where Cisco are now with their 'tin' approach to where Cisco could be with an 'IaaS' approach is huge. This conversation goes way beyond my WLAN blog....
Final word... I'm fortunate enough to be a member of the Cisco Mobility PVT. So I hope to be able to report back about the good things are going to emerge from Cisco in the near future. Watch this space...
Mental note! Get CCIE before Meraki technology is added to the exam...